The Rise of SaaS Applications: Effective Access Control
The world of business technology is rapidly evolving, with Software as a Service (SaaS) applications leading the charge in digital transformation. These cloud-based solutions have revolutionized how organizations operate, offering unparalleled convenience, scalability, and cost-effectiveness. As more companies embrace the power of SaaS, a critical challenge arises – ensuring robust access control measures to protect sensitive data and maintain compliance.
In this era of widespread cyber threats and stringent regulations, implementing effective SaaS access control has become a paramount concern for organizations across industries. By controlling who can access specific applications, data, and functionalities within a SaaS environment, businesses can mitigate the risks of unauthorized access, data breaches, and potential legal and financial consequences.
This comprehensive guide delves into the realm of SaaS applications, exploring their benefits, challenges, and the crucial role of SaaS access control in safeguarding operations. From understanding the fundamentals of SaaS to implementing cutting-edge access control strategies, this article equips readers with the knowledge and insights necessary to navigate the ever-evolving landscape of cloud technologies securely and efficiently.
Note:
Find additional insights on SaaS application in our article “How is SaaS Software Distibuted“.
Understanding SaaS Applications
SaaS applications are software solutions hosted and maintained by third-party providers. Instead of installing and running programs locally, users access these applications over the internet, typically through web browsers or dedicated apps. This delivery model eliminates the need for on-premises hardware and software installations, reducing IT overhead and maintenance costs.
What is a SaaS Application?
A SaaS application is a software solution that is hosted and delivered over the internet by a third-party provider. Unlike traditional on-premises software, which requires installation and maintenance on local servers or computers, SaaS applications are accessed through web browsers or dedicated apps. The provider is responsible for managing the application’s infrastructure, security, and updates, while users pay a subscription fee to access and use the software.
Benefits of SaaS Applications
- Accessibility: SaaS applications can be accessed from anywhere with an internet connection, enabling remote work and collaboration.
- Scalability: Organizations can easily scale their SaaS usage up or down based on their changing needs, without investing in additional infrastructure.
- Cost-effectiveness: SaaS providers handle software updates, maintenance, and infrastructure costs, reducing the financial burden on businesses.
- Automatic Updates: SaaS applications are regularly updated by the providers, ensuring users have access to the latest features and security patches.
The Importance of SaaS Access Control
As organizations increasingly rely on SaaS applications to streamline operations and store sensitive data, implementing robust SaaS access control measures becomes crucial. SaaS access control refers to the mechanisms and policies that govern who can access specific applications, data, and functionalities within a SaaS environment.
Key Benefits of SaaS Access Control
- Data Security: By controlling access to sensitive information, organizations can protect against unauthorized access, data breaches, and potential legal and financial consequences.
- Compliance: Many industries have strict regulations regarding data privacy and security. SaaS access control helps organizations maintain compliance with these regulations.
- User Management: SaaS access control simplifies the process of granting, modifying, and revoking access rights for employees, contractors, and third-party vendors.
- Productivity: By ensuring that users have access to only the applications and data they need, SaaS access control can improve productivity and minimize distractions.
Implementing Effective SaaS Access Control
Establishing a comprehensive SaaS access control strategy involves several key components:
Identity and Access Management (IAM)
IAM solutions enable organizations to centrally manage user identities, authentication, and authorization processes. By integrating IAM with SaaS applications, businesses can enforce consistent access policies across their entire SaaS ecosystem.
IAM solutions typically include the following core functionalities:
- User Provisioning: Automating the creation, modification, and deactivation of user accounts across multiple SaaS applications, ensuring proper access rights are granted or revoked in a timely manner.
- Single Sign-On (SSO): Allowing users to access multiple SaaS applications with a single set of credentials, enhancing security and usability.
- Access Governance: Defining and enforcing access policies based on user roles, responsibilities, and risk factors, ensuring compliance with organizational policies and regulatory requirements.
- Directory Services: Maintaining a centralized repository of user identities and attributes, enabling efficient management and synchronization across different systems.
- Reporting and Auditing: Providing detailed logs and reports on user activities, access events, and policy violations, enabling effective monitoring and incident response.
By implementing a robust IAM solution, organizations can streamline user management processes, improve security posture, and maintain better control over their SaaS application landscape.
(Source: Amazon Web Services, aws.amazon.com)
Multi-Factor Authentication (MFA)
MFA adds an extra layer of security by requiring users to provide multiple forms of authentication, such as a password and a one-time code sent to their mobile device. This approach significantly reduces the risk of unauthorized access, even if one authentication factor is compromised.
Common MFA factors include:
- Knowledge factors (e.g., passwords, PINs)
- Possession factors (e.g., one-time codes sent to a mobile device, security keys)
- Inherence factors (e.g., biometrics like fingerprints, facial recognition)
By combining multiple factors, MFA ensures that even if one factor is compromised, unauthorized access is still prevented. Organizations should implement MFA for all SaaS applications that handle sensitive data or critical business functions.
Role-Based Access Control (RBAC)
RBAC is a widely adopted access control model that assigns permissions based on an individual’s role within the organization. By defining roles and associated access rights, organizations can easily manage access to SaaS applications and data, minimizing the risk of over-privileged accounts.
In an RBAC model, roles are created based on job functions and responsibilities. Users are then assigned to these roles, inheriting the corresponding permissions and access rights. This approach simplifies access management, as permissions can be granted or revoked based on role changes, rather than modifying individual user accounts.
RBAC also supports the principle of least privilege, ensuring that users only have access to the resources and functionalities necessary for their roles, reducing the potential for unauthorized access or misuse.
(Source: AWS Blog, aws.amazon.com/blogs)
Auditing and Monitoring
Regularly auditing and monitoring user activities within SaaS applications is crucial for identifying potential security threats and ensuring compliance. Log analysis and real-time monitoring can help detect suspicious behavior and enable prompt incident response.
Auditing and monitoring capabilities should include:
- Detailed logging of user activities, including login attempts, data access, and configuration changes.
- Real-time alerts and notifications for suspicious or unauthorized activities.
- Centralized log management and analysis tools for efficient review and investigation.
- Compliance reporting to demonstrate adherence to regulatory requirements.
By implementing robust auditing and monitoring practices, organizations can quickly identify and respond to potential security incidents, minimize the impact of data breaches, and maintain a strong security posture.
Employee Training and Awareness
Educating employees on the importance of data security and best practices for SaaS access control is essential. Regular training and awareness campaigns can help mitigate the risk of human error, which is often a leading cause of data breaches.
An effective employee training and awareness program should cover the following aspects:
- SaaS Security Policies and Procedures: Employees should be thoroughly trained on the organization’s security policies, procedures, and guidelines related to SaaS applications. This includes acceptable use policies, password management best practices, and incident reporting protocols.
- Identifying and Reporting Security Threats: Training should equip employees with the ability to recognize potential security threats, such as phishing attempts, suspicious emails, or unauthorized access attempts. Employees should be aware of the proper channels for reporting such incidents promptly.
- Data Handling and Privacy Practices: Employees should understand the importance of protecting sensitive data and maintaining privacy standards. This includes guidance on handling customer information, proprietary data, and compliance with relevant regulations (e.g., GDPR, HIPAA).
- Role-Based Access Control (RBAC): Employees need to understand the RBAC model implemented within the organization and the importance of adhering to their assigned roles and associated permissions. This helps prevent accidental or intentional misuse of access privileges.
- Multi-Factor Authentication (MFA): Training should cover the proper use of MFA methods, such as mobile authenticator apps or hardware security keys, and the importance of keeping these factors secure.
- Continuous Reinforcement: Security awareness should be an ongoing process, with regular refresher training sessions, security newsletters, and updates on emerging threats and best practices.
Organizations can leverage various training methods, including classroom sessions, online courses, simulated phishing exercises, and hands-on workshops, to ensure employees are well-equipped to handle SaaS access control and security responsibilities.
By fostering a strong security culture and providing employees with the necessary knowledge and skills, organizations can significantly reduce the risk of human error and create a more secure SaaS environment.
Real-World Examples of SaaS Access Control
Many organizations across various industries have implemented SaaS access control measures to enhance their security and operational efficiency. Here are a few examples:
- Healthcare Industry: Healthcare providers leverage SaaS access control to protect sensitive patient data and ensure compliance with regulations like HIPAA. Role-based access controls and MFA are commonly used to restrict access to electronic medical records (EMRs) and other critical applications.
- Financial Services: Banks and financial institutions implement robust SaaS access control measures to safeguard customer data and comply with strict regulations. IAM solutions, MFA, and auditing capabilities are essential for managing access to financial applications and preventing unauthorized transactions.
- E-commerce: Online retailers utilize SaaS access control to protect customer data, such as payment information and purchase histories. By implementing RBAC and MFA, they can restrict access to sensitive data and prevent unauthorized modifications to their e-commerce platforms.
SaaS Access Control and Cost Management with Binadox
While implementing robust SaaS access control measures is crucial for data security and compliance, it’s also essential to manage and optimize SaaS spending effectively. Binadox offers a comprehensive solution that combines access control capabilities with cost management tools, empowering organizations to streamline their SaaS operations securely and cost-effectively.
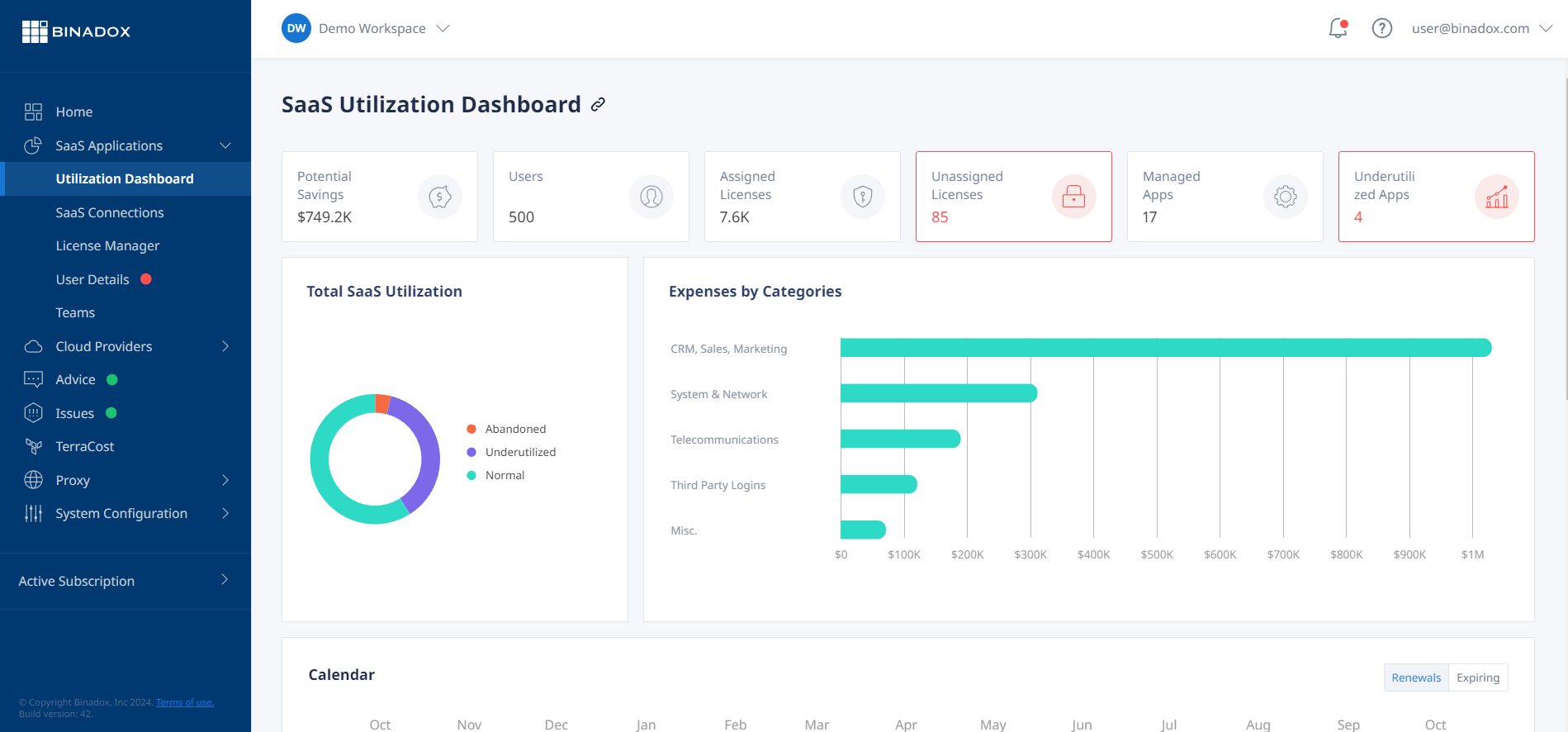
(Source: Binadox, binadox.com)
Binadox’s SaaS Access Control Features
Binadox’s SaaS access control features include:
- Centralized User Management: Binadox provides a centralized platform to manage user identities, roles, and access permissions across all SaaS applications within an organization. This streamlines the user provisioning and deprovisioning processes, ensuring timely access updates and minimizing security risks.
- Single Sign-On (SSO) Integration: Binadox integrates with popular SSO providers, enabling users to securely access multiple SaaS applications with a single set of credentials. This enhances usability while maintaining robust authentication measures.
- Role-Based Access Control (RBAC): Binadox supports RBAC, allowing organizations to define roles based on job functions and assign appropriate access permissions. This ensures that users have access only to the SaaS applications and data they need, reducing the risk of over-privileged accounts.
- Auditing and Reporting: Binadox provides detailed auditing and reporting capabilities, enabling organizations to track user activities, monitor access events, and identify potential security threats or policy violations.
SaaS Cost Management and Optimization
In addition to access control features, Binadox offers powerful cost management tools to help organizations optimize their SaaS spending:
- SaaS Discovery and Inventory Management: Binadox automatically discovers and catalogs all SaaS applications used within an organization, providing a comprehensive view of the SaaS landscape and associated costs.
- License Optimization: By analyzing user activity and license utilization, Binadox helps organizations identify underutilized or redundant licenses, enabling cost savings through license optimization.
- Spending Analytics and Reporting: Binadox provides detailed spending analytics and reports, allowing organizations to track SaaS costs, identify cost drivers, and make data-driven decisions for cost optimization.
- Vendor Management: Binadox simplifies vendor management by consolidating SaaS contracts, renewals, and invoices in a single platform, enabling better negotiation and cost control.
By combining robust SaaS access control measures with cost management capabilities, Binadox empowers organizations to maintain a secure and compliant SaaS environment while optimizing their SaaS spending and maximizing return on investment.
You can learn how to maximize efficiency in software subscriptions in our other article.
Binadox Tools for SaaS Cost Management
While implementing robust SaaS access control measures is paramount for data security and compliance, organizations must also prioritize effective SaaS cost management to optimize their software spending and maximize return on investment. Binadox offers a comprehensive suite of tools designed to streamline SaaS cost management processes.
With Binadox, businesses can automatically discover and catalog all SaaS applications used within the organization, providing a centralized view of their SaaS landscape and associated costs. Advanced analytics and reporting capabilities enable data-driven decision-making, helping organizations identify cost drivers, optimize license utilization, and eliminate redundant or underutilized subscriptions.
Binadox also simplifies vendor management by consolidating SaaS contracts, renewals, and invoices in a single platform, empowering organizations to negotiate better terms and exercise tighter cost control. By combining access control capabilities with robust cost management tools, Binadox offers a comprehensive solution for securing and optimizing an organization’s SaaS operations.
Renewals Calendar
Binadox offers a powerful subscription tracking tool that helps organizations stay on top of their SaaS costs by providing visibility into active subscription expirations and associated renewal expenses.
This tool helps track the expiration dates of active subscriptions and the expenses associated with their renewals on a specific date. By having this information readily available, businesses can proactively manage their SaaS spend and avoid unexpected costs or lapses in service.
The subscription tracking tool displays the expiration dates of active subscriptions and the costs of renewal on an intuitive calendar view. When hovering over a specific date on the calendar, users can see a breakdown of the SaaS applications with licenses expiring on that day, along with the renewal costs for each application.
This granular level of detail empowers organizations to plan their budgets effectively and ensure timely renewals for critical SaaS tools.
By leveraging Binadox’s subscription tracking capabilities, companies can streamline their SaaS cost management processes, eliminate surprises, and make informed decisions regarding their software investments.
(Source: Binadox, binadox.com)
Usage Intensity
Binadox offers an insightful application usage analytics tool to help organizations identify rarely used SaaS applications, enabling efficient optimization of software subscriptions and associated costs.
This powerful tool assists in identifying SaaS applications with low usage patterns, allowing businesses to streamline their software portfolio and minimize unnecessary expenses. By pinpointing underutilized applications, organizations can make informed decisions about which subscriptions to renew, downgrade, or discontinue, leading to significant cost savings and improved resource allocation.
The application usage analytics tool presents a visually compelling graph that represents the usage intensity of each SaaS application within the organization. The darker the color on the graph, the more heavily that particular application was used on a given day. This intuitive representation provides a clear overview of application usage patterns, making it easy to identify applications that are rarely accessed or utilized.
By leveraging Binadox’s application usage analytics capabilities, companies can gain valuable insights into their SaaS landscape, ensuring that they are not paying for subscriptions that offer minimal value to their operations. This data-driven approach empowers organizations to optimize their software investments, reduce wasteful spending, and allocate resources more effectively.
(Source: Binadox, binadox.com)
Advice
Binadox offers a powerful recommendation engine that provides personalized guidance on optimizing your cloud infrastructure for enhanced savings, security, and effective planning.
This innovative tool leverages the data from your connected SaaS applications and cloud providers to conduct in-depth analyses and generate tailored recommendations across three key categories: savings, security, and planning. By identifying potential areas for improvement, Binadox empowers you to make informed decisions and maximize the efficiency of your cloud operations.
For your convenience, Binadox allows you to set up customized notifications, ensuring you stay informed about critical recommendations. Additionally, you can choose to place specific recommendations on an ignore list, preventing repeated visibility of advice that may not be relevant to your current needs.
Each recommendation provided by Binadox is accompanied by comprehensive details, including its parameters, a detailed explanation of the advice, and a list of licenses it covers. This level of transparency ensures you have a thorough understanding of the recommendations, enabling you to make well-informed decisions aligned with your organization’s unique requirements.
By leveraging Binadox’s Advice tool, you can proactively optimize your cloud infrastructure, reduce costs, enhance security measures, and streamline planning processes, ultimately maximizing the value of your cloud investments and driving operational excellence.
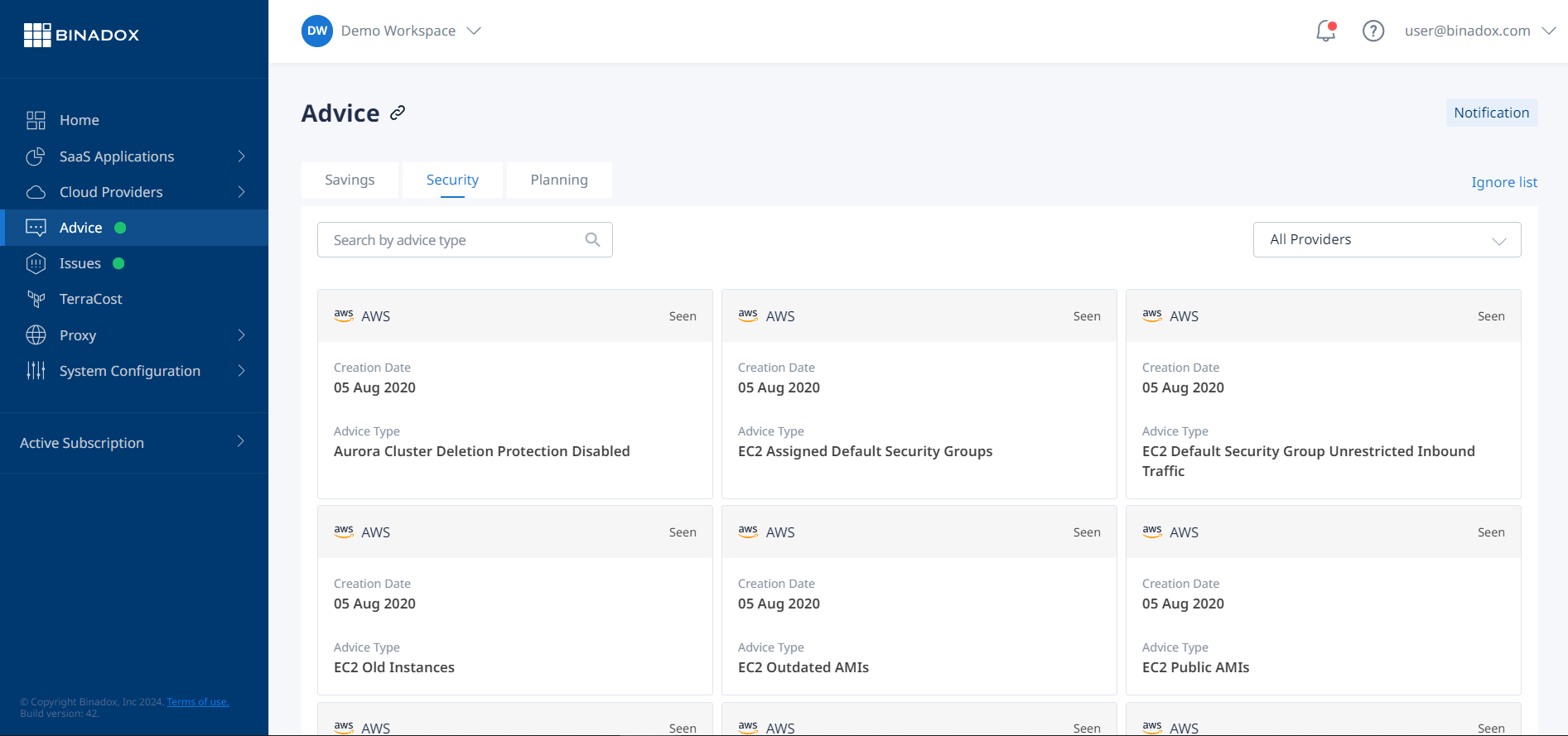
(Source: Binadox, binadox.com)
License Manager
Binadox offers a robust License Manager tool that helps organizations identify and eliminate ineffective applications, thereby optimizing their software spending.
This tool simplifies the evaluation process by displaying a comprehensive table of applications with key parameters such as billing period and plan, number of licenses, percentage utilization rate, next renewal date, and upcoming payment. By providing this detailed view, organizations can easily assess the value and performance of each application.
The License Manager tool enables businesses to make informed decisions about which subscriptions to retain or eliminate, ensuring they are only investing in applications that deliver tangible benefits. This proactive approach helps reduce unnecessary expenses and improve overall efficiency, ultimately maximizing the value of their software investments.
(Source: Binadox, binadox.com)
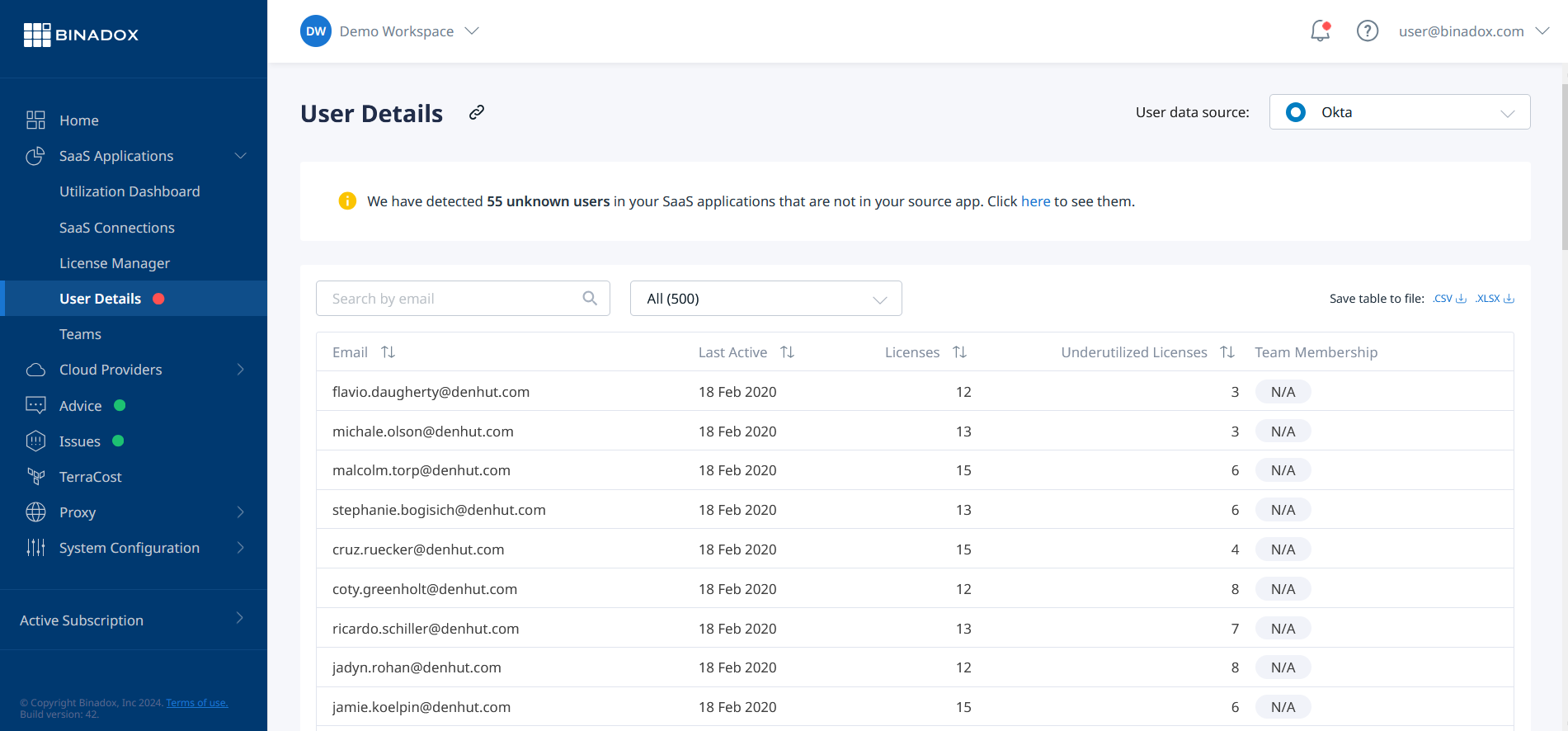
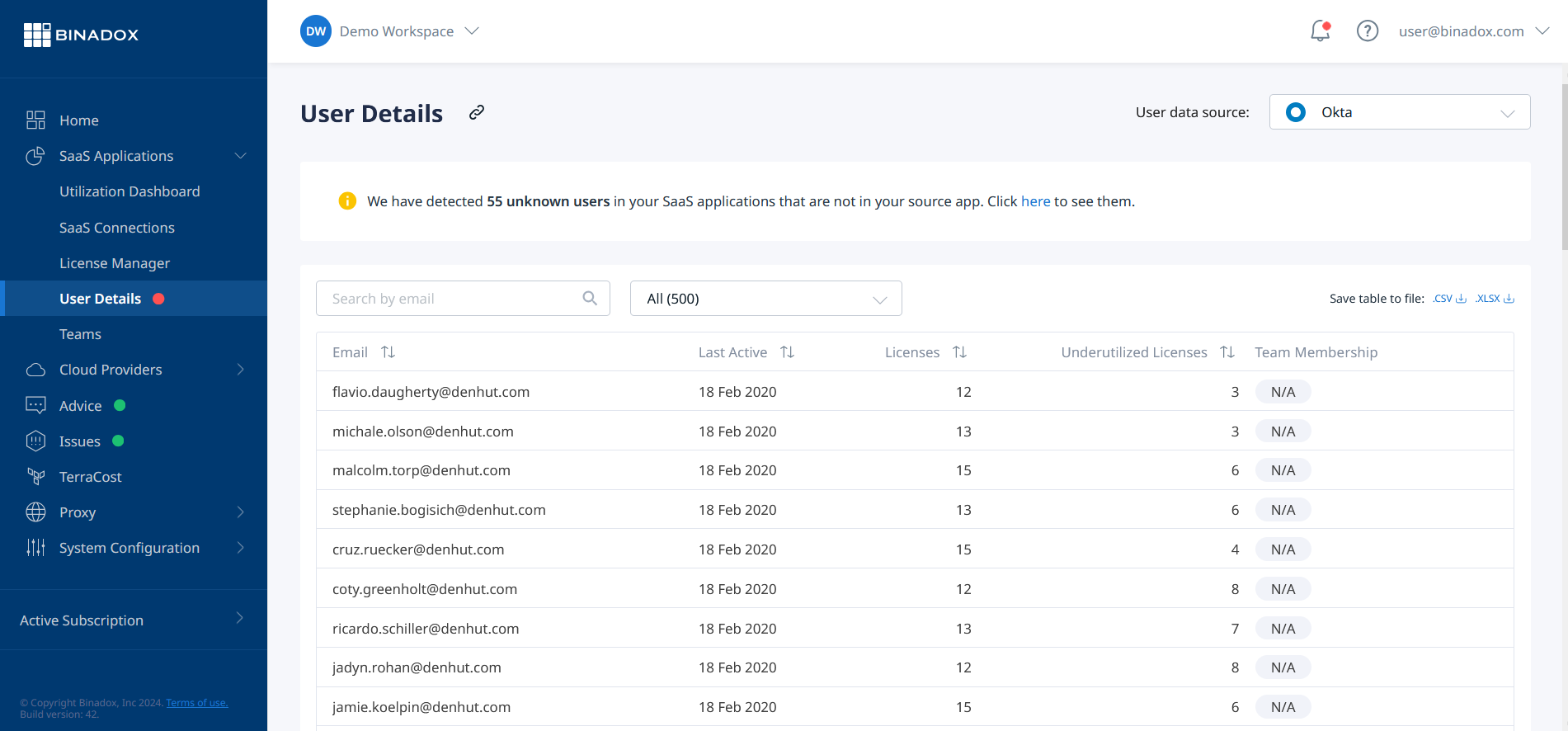
User Details
Binadox offers an insightful User Details tool that highlights ineffective use of licenses by employees, enabling organizations to optimize their software investments.
This tool provides a detailed table of users along with their usage statistics, including the date of last activity, number of licenses available, amount of underutilized licenses, and team membership. This comprehensive view allows organizations to quickly identify and address areas of inefficiency.
By delving into individual user statistics, organizations can gain granular insights into each user’s application usage. The detailed table includes parameters such as app utilization, last activity date, billing period, and plan. This level of detail empowers businesses to make informed decisions about license allocation and ensure that resources are being utilized effectively.
Leveraging Binadox’s User Details tool, organizations can monitor and analyze employee license usage, identify underutilized resources, and implement strategies to optimize their software expenditures, ultimately enhancing the overall value of their software investments.
(Source: Binadox, binadox.com)
Teams
Binadox offers a robust Teams tool that enables organizations to distribute costs across teams and analyze the effectiveness of license usage within specific teams.
This tool streamlines cost allocation and provides detailed insights by displaying a comprehensive table of all teams. Team composition information is seamlessly pulled from Office 365, GSuite, or Okta, ensuring accurate and up-to-date data. The table includes key information such as the number of members in each team, available applications, and quantities of unassigned licenses.
Additionally, the Teams tool provides notifications if there are individuals not assigned to any team, along with recommendations to check the settings of collaborative applications. This proactive approach helps organizations ensure that all licenses are effectively utilized and that collaborative tools are properly configured.
By leveraging Binadox’s Teams tool, businesses can efficiently manage license distribution, monitor team-specific usage, and implement strategies to optimize their software investments, ultimately enhancing operational efficiency and cost-effectiveness.
(Source: Binadox, binadox.com)
Conclusion
As the adoption of SaaS applications continues to accelerate, organizations must prioritize robust access control measures to safeguard their data, maintain compliance, and ensure operational efficiency.
The implementation of Identity and Access Management (IAM) solutions, Multi-Factor Authentication (MFA), Role-Based Access Control (RBAC), auditing and monitoring capabilities, and comprehensive employee training programs are essential components of an effective SaaS access control strategy.
By embracing these best practices, businesses can harness the full potential of SaaS applications while mitigating risks and minimizing the chances of data breaches and unauthorized access. Moreover, by partnering with solutions like Binadox, organizations can seamlessly integrate access control measures with cost management tools, optimizing their SaaS spending and maximizing their return on investment.
As the digital landscape continues to evolve, staying ahead of emerging threats and adopting cutting-edge security practices will be crucial for organizations to maintain a competitive edge while ensuring the integrity and confidentiality of their data and operations. By prioritizing SaaS access control and leveraging the right tools and strategies, businesses can navigate the ever-changing technology landscape with confidence and resilience.
To gain a deeper understanding of cloud technologies, visit the Binadox blog. This blog offers comprehensive insights and up-to-date information on various cloud computing topics.

