What’s shadow IT?
Shadow IT refers to IT resources (devices, software, services) used by employees without the explicit permission of the organization’s IT department. Either the technology is not approved by the IT specialists or they’re simply unaware that a business unit is using new software or subscribing to a cloud service. Most organizations heavily underestimate the scale of shadow IT adoption. Usually, workers use a huge number of software products and services CIOs don’t know about, not to mention the approval of these SaaS applications.
According to Stratecast and Frost & Sullivan’s survey on shadow IT, more than 80% of employees admit using non-approved SaaS applications to fulfill their work-related responsibilities and on average 35% of all SaaS apps in the company are purchased and used without notifying anyone in the IT department.
Interestingly enough, the survey also reveals that IT employees themselves are more prone to using non-approved SaaS applications than a line of business employees.
How shadow IT appears in a company?
A high proportion of shadow IT applications are cloud-based and do not require direct IT involvement for deployment and installment.
The initial aim of using shadow IT resources is obvious – employees working in a company want to get their jobs being done in a more efficient way. That makes business units use new systems that are acquired faster and easier. Additionally, workers can use their own budget to purchase dedicated applications and subscribe to services without additional financial requests from the IT department.
The second reason why shadow IT has become commonplace is the blending of personal and business use of devices and applications, especially among the younger and more mobile workforce. Employees expect to be able to use for work personal mobile devices and SaaS which they use at home. This Bring Your Own Device (BYOD) trend encourages employees to use their personal devices (smartphones, tablets, PCs) to process corporate data. Personal devices are used to access the company’s email, internal services, address books, calendars, etc.
This ‘work anywhere’ concept positively impacts employee productivity, creates a more flexible workplace, and is generally supported by top management. On the other hand, with the usage of personal devices and the installation of unsanctioned applications, employees unwillingly subject their company to unexpected security issues. Let’s now explore the risks and benefits of Shadow IT in detail.
Shadow IT risks
1. Unnecessary exposure to security breaches
The emergence of shadow IT has brought significant changes in the enterprise security landscape challenging IT groups with new scenarios they were not exposed to before. Increased use of unapproved file-sharing services, remote administration tools, and other third-party applications incorporate environment can lead to security breaches unknown to the internal IT department, as it is nearly impossible to track all the services and apps (especially mobile apps) being used by the company employees.
A shadow IT application may have a vulnerability that can be exploited by an attacker to access the corporate network and data. Considering that many team members use two or more devices for work, the possibility of a security breach is immense because each device is a potential point of entry for intruders.
2. Additional data security
Retaining control over data within an organization is already a challenge internal IT departments have to deal with on a daily basis. With cloud and mobile services, this challenge becomes greatly magnified. When files are stored in and transmitted via public cloud services and unsanctioned mobile apps, business data is placed outside of the organization and it becomes impossible to control the data or even know who accesses it.
Sensitive and unencrypted information floats outside of controlled corporate channels, so it is just a matter of time when it gets in the wrong hands. Lack of control results in data inaccuracy, unauthorized or blocked access, data leaks, and data loss.
3. Enterprise regulatory compliance issues
Most employees adopt shadow IT apps without a clear understanding of the organization’s data security and compliance challenges and requirements. Compliance standards such as PCI-DSS, HIPAA, GLBA, FISMA/NIST, CobiT, and others govern the use and transmission of confidential and sensitive information.
When data is processed by external applications without noticing executives or approval of the in-house IT, it is potentially exposed to unauthorized access and violation of the corporate and regulatory compliance requirements. Employees may unknowingly violate data privacy regulations simply by storing business data in the wrong cloud service.
Failing to handle and protect sensitive information according to industry standards leads to potential compliance complications and fines and can cost dearly to resolve.
4. Hidden costs
Shadow IT can mean unexpected problems to the financial health of an organization. First of all, it can significantly increase overall IT operations expenses due to hidden costs, which are typically 4-8 times higher than visible costs.
These are the costs that public cloud providers charge above the sticker price, costs of security issues, data security, operations, integration with cloud services, network issues, and vendor management. Add also financial liabilities in case of data security incidents: security remediation, auditing processes, notification penalties, brand damage, etc.
Another issue is duplicated technologies. Different business units buy their own solutions and use their own budgets to acquire software. Without single-entry control, IT departments are unaware of how many services are being used, or how many services are being paid for on the whole.
Not controlled by the in-house IT redundant technologies multiply across the organization and lead to missed opportunities for bulk pricing. If uncontrolled, shadow IT creates inefficiencies, security risks, compliance gaps, wastes money, and can quickly mount into costly complications.
The good news is that as with everything there is also another side of the medal.
Shadow IT Benefits
Even if employees recognize the problems connected with the use of unapproved software and services, they feel that the risks mentioned are totally justified. Shadow IT, indeed, can bring various real benefits to the companies and employees, if properly managed. It allows to avoid inefficient corporate processes, gain business agility, and increase productivity.
1. Boost productivity
Business units turn to shadow IT seeking to be more mobile and access business data whenever they need it. Employees expect to have the ability to bring their work with them out of the office and off the local network.
Cloud and mobile technologies provide this opportunity – they make data available from any location and device and allow to share the files easily with colleagues and outside business partners. No wonder, that cloud-based file-sharing services are among the most popular non-approved apps.
2. Effective solutions aligned with business needs
Another reason why business units adopt shadow IT is to take on business problems fully equipped. The increasingly growing market of business applications constantly offers new solutions. Ultra-modern technologies make things easier and drive value, especially in industries where innovations are welcomed.
IT groups are not always successful in handling end-user requests for new solutions: internal application development is a long process and purchasing of external solutions doesn’t always satisfy the business needs. When business units request solutions from IT, the specific details can be miscommunicated or omitted and, as a result, the finished product isn’t exactly what was requested.
Shadow IT alternative allows to get around strict corporate policies and get the solutions closely aligned with a specific business need. When users are the ones choosing solutions, it is easier to keep up with industry trends and find the tools that better suit the original goal.
3. Lessening the burden on the IT department
Allowing the staff to freely choose their own apps and services minimizes the drain on the IT department and stimulates employee engagement, which ultimately helps the business.
In the SaaS model, the software vendor is responsible for hosting and maintaining applications, for backup and recovery of data. This removes a burden from IT groups, lets them focus on other, mission-critical tasks, and allows them to avoid capital investments in infrastructure and maintenance.
With shadow IT, end users have access to a variety of solutions without administrative restrictions standing in their way. It helps to avoid viewing IT groups as an obstacle, which is quite common in many businesses. It’s a win-win situation for both IT groups and business units.
Sum up
Along with compliance concerns and risks that shadow IT poses to the security of an organization, there are some real benefits that add value and bring innovation. First of all, it is an effective way to highlight inefficiencies in decision-making processes and identify the weaknesses that caused the need for unapproved software in the first place.
Second of all, beyond the initial set of challenges, shadow IT brings new opportunities to improve traditional ways employees approach software issues and communicate with in-house IT departments.
In the long run, shadow IT is not necessarily a terrible thing. It is just another business reality, which should not be overlooked, but managed.
Manage Shadow IT with Binadox
Binadox automatically detects all SaaS applications that employees are using. This platform helps turn every single benefit to your advantage while removing every single drawback. It provides necessary tools for analyzing and monitoring SaaS applications so you know what applications should be allowed, restricted, or shared within your company.
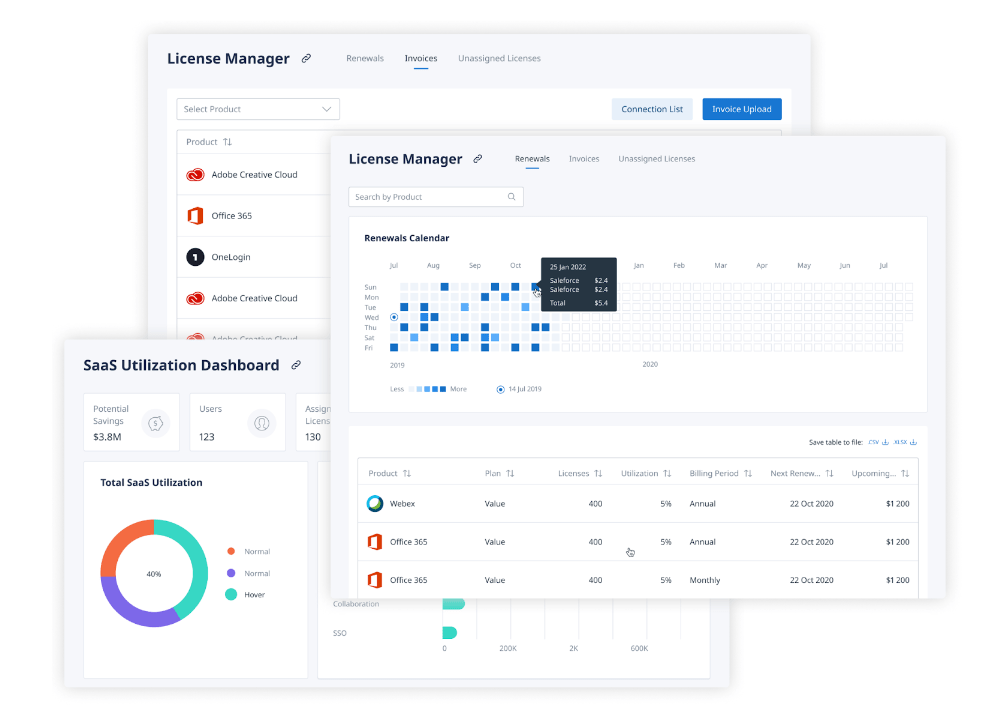
Binadox also provides information that is useful for numerous departments in your company: IT department, Accounting and Finance, Human Resource Management department, and others. Therefore, you can ensure license compliance, minimize security risks, and keep your employees productive and your business flexible.
Sign up for Binadox free trial or book a demo to see how we can help.

